Move along high-tech spyware and sophisticated gizmos - figuring out how to hack someone’s phone remotely is a lot easier than you think in 2020. Hacking someone's phone without touching it by sending over a link or with a computer has been commonplace for a while, but technological advances have since taken the science fiction out of how to hack someone’s phone remotely.
No surprise that hacking someone’s phone remotely is such a prevalent issue today. Between March to September last year, many phone users were hacked because of Whatsapp exploits, website-embedded malware and virus-laden online videos. Remote mobile phone hacks have already become an everyday reality.
How to hack someone's phone remotely - before we begin....
There are really only two smartphone operating systems largely in use today - iOS for Apple devices like iPhone and iPad, and Android. Here's a quick rundown of both OSes.
iOS
- Developed by: Apple Inc.
- Devices include: iPods, iPhones,iPad, Apple TV
- First Released on: 29 June 2007 (simultaneous launch with the Original iPhone)
Android
- Developed by: Google, Open Handset Alliance
- Devices Include: LG, Oppo, Sony, Xiaomi, Samsung, Motorola
- First released on: 23 September 2008
Many of you reading this are probably new to hacking mobile phones, so we'll talk about beginner-friendly remote mobile hacking apps and software, as well remote mobile hacking techniques frequently used by hackers without touching your phone.
These software and techniques don't require a lot of technical know-how, and using them is more straightforward than having to fiddle with a garbled mess of code.
Here are a few other questions you might want to ask beforehand:
how to hack someone’s phone remotely - Key Questions to Ask
Question 1: When I hack a device, what can I actually receive or see?
The range of mobile data you can collect varies between different software and techniques, but on the whole you'll likely be able to track:
- The hacked phone's location (via GPS)
- Call records. Some software like phone spying apps can also include detailed date and timestamps.
- Keystrokes done by the user (for keylogging software). Keystrokes basically refer to a person's interactions with the mobile keyboard, and tracking keystrokes is one way mobile hackers obtain usernames and passwords to personal accounts.
- Text message history. All text messages - deleted, old or new - can be viewed by the hacker.
- Emails. This exposes not just email content, but the addresses emails were sent to.
- Internal Media. That means all images, videos, recordings and other files stored in your phone.
- Internet History. This means all sites accessed, typically regardless of whether the hacked phone has had its data cache regularly wiped or not.
- Contact Lists. Mobile hackers can use contact information to impersonate close contacts or pass misinformation.
- Social Media usage. Many of our social media accounts are deeply integrated with our mobile phones, and mobile hackers can easily view all of our interactions on these sites by hacking mobile phones remotely.
Question 2: Can all mobile devices be remotely hacked?
The simple answer is YES. Any device can be hacked without hackers actually touching it, especially if it is not updated to the latest version of an operating system, or is connected to an external public network that exposes the device to potential intrusion, like a false WiFi network.
Take note - whether you are using an iPad or iPhone (5 to X) running on iOS or an phone running on Android ( 3 to 9), you will be susceptible to mobile hackers hacking your phone remotely if you do not take the necessary precautions.
Question 3: Are the 5 ways for hacking someone's phone remotely detectable?
Phone-spying apps are typically not detectable by person using the hacked phone, since they leave not much trace of operating in the background.
Other forms of hacking somebody's phone without physical contact are more easily detectable, like malware and control messages.
Still, mobile hackers wouldn't be considered such a menace if they left loopholes and clues for their victims to discover. On the whole, these remote mobile hacking techniques are very often difficult to detect by everyday users.
Question 4: Should I try hacking my own phone?
Not with some of the ways we will discuss here of course, but doing so with spyware might be an excellent idea.
Spyware as a geo-location feature that tracks the hacked phone's position, and can copy data off the hacked device. While you may have to root or jailbreak your phone in order to get spyware to work, this means
- You don't have to worry about your phone being stolen or lost since the spyware will accurately pinpoint its location
- You have a data backup in case your phone is damaged beyond repair or compromised in some other way.
Question 5: Which phone spying app is the best then?
There are many different versions of spyware available today, and ideally what you will want is a spying app that:
- doesn't require you to root or jailbreak your phone
- gives you the most amount of tracked data
- doesn't cost you too much
- is supported by the Apple / Google Play Store
Based on user reviews and general consensus, we recommend the following phone spying apps:
(1). For iPhone: Spyic
(2). For Android: XNSpy / Google Family Link (Free but less features)
(3). For excellent location tracking: Geozilla
(4). For best-in-class data recovery: DDI Utilities
(5). Overall best: XNSpy
Question 6: Are all forms of mobile phone hacking illegal?
No, not all forms of remote mobile phone hacks are illegal. Some, like malware, control messages and false Wi-Fi networks are clearly flouting the law. But others, like spyware and IMSI catchers can be used in perfectly legal ways.
Examples of when these technologies are used legally include:
- Employers tracking their employee's work - related activities to ensure productivity and proper use of company resources WITH the explicit consent of their employees.
- Two individuals monitoring each other's mobile phone activity WITH each other's consent.
- Parents monitoring their child's / ward's mobile phone activities and location without their consent. A child is designated as an individual who is younger than 18 years of age.
- Use of IMSI catchers by law enforcement agencies to track criminal / terrorist activity to adequately carry out security operations.
Whether hacking someone's phone remotely is ethical or not again depends on how it is used.
How to hack someone’s phone remotely in 5 ways
Hack 1. Using malicious software like SIMJacker to hack into someone’s phone

When looking at how to hack someone's phone remotely, Malicious software, or malware, definitely deserves a mention. Most of us are certainly not strangers to mobile phishing scams or ransomware, but malware can also hide behind the façade of random videos on social media and unverified web links.
Different forms of malware are all designed to infringe on your personal privacy and safety. Most steal personal data or monitor activity on your mobile phone, and more dangerous types can even render your mobile phone completely unusable. SIMjacker, for example, exploited a vulnerability in some SIM cards to take control over the victim's mobile phone. Another similar malware is WIBattack, which takes advantage of the same weaknesses in some SIM cards.
To minimize the risk that malware poses to your mobile phone, be sure to install an anti-virus software and refrain from accessing unverified links and pages.
Hack 2. Using spyware like Spyfone to hack into mobile phones
Designed as ideal answers to how to hack someone's phone remotely, phone spying software is becoming accepted by concerned parents and scrutinizing employers alike.
Not all spyware are created equal. Spyfone, a highly popular phone monitoring software, is able to monitor not only calls and contacts, but also geolocation, photo/video and social media. In general, mobile phone hacking apps typically possess these traits:
(1). They work in the background, which makes them incredibly hard to detect to the average user.
(2). They have call, location and messaging tracker services (to varying degrees of accuracy)
(3). Most require users to jailbreak (for iOS) or root (for Android) their phones. Both basically mean bypassing certain limits and restrictions built in by the developer, and doing either presents security risks to the user’s own phone. For a more in-depth explanation, take a look at Android central’s read on rooting and Digital Trend’s primer on jailbreaking 101.
Hack 3. Using "man-in-the-middle" attacks on public Wi-Fi to hack into mobile phones nearby

In today’s data-guzzling world, being in range of a public Wi-Fi network is analogous to chancing upon a miracle spring in the desert. But are public Wi-Fi networks a godsend, or a ploy for something more sinister?
Savvy hackers can set up rogue Wi-Fi networks that mimic the legitimate ones to lure unsuspecting users in. Once a user has connected to the false network, hackers then conduct what is known as a “man in the middle” attack to deceive users into revealing potentially sensitive information. On these fake networks, hackers gain full visibility over what you are looking at and doing on your device.
To illustrate this, imagine using a public Wi-Fi network to access your bank account. You key in your credentials, and everything seems to be responding fine – until you realise your bank account is completely empty.
Hack 4. Sending control messages via SMS to hack into a mobile phone
It turns out that even receiving SMSes can open a door for hackers to step into and take control of your phone. How to hack someone’s phone remotely using SMSes often comes in two ways: Midnight Raids and Control Message Attacks.
Midnight raids get their namesake from the fact that these are often done in the dead of night when phone users have turned in and their mobile phones are left charging. By sending a simple text message, hackers can control web browsers on mobile phones and use them as a means to siphon personal data away, or even transmit viruses.
Control Message Attacks also give hackers high levels of control over the target mobile phone, but they do so with what is called a control message that grants the hacker access to a mobile phone’s settings.
The good news is, mobile phone software developers are aware of this risk and regularly update and issue patches to minimize risk. The bad news is, phone users don’t really have the means to prevent these sorts of hacks altogether, and it’s mostly up to the developers to make sure hackers don’t exploit the flaw to its fullest extent.
Hack 5. Hacking into a mobile phone using an IMSI Catcher
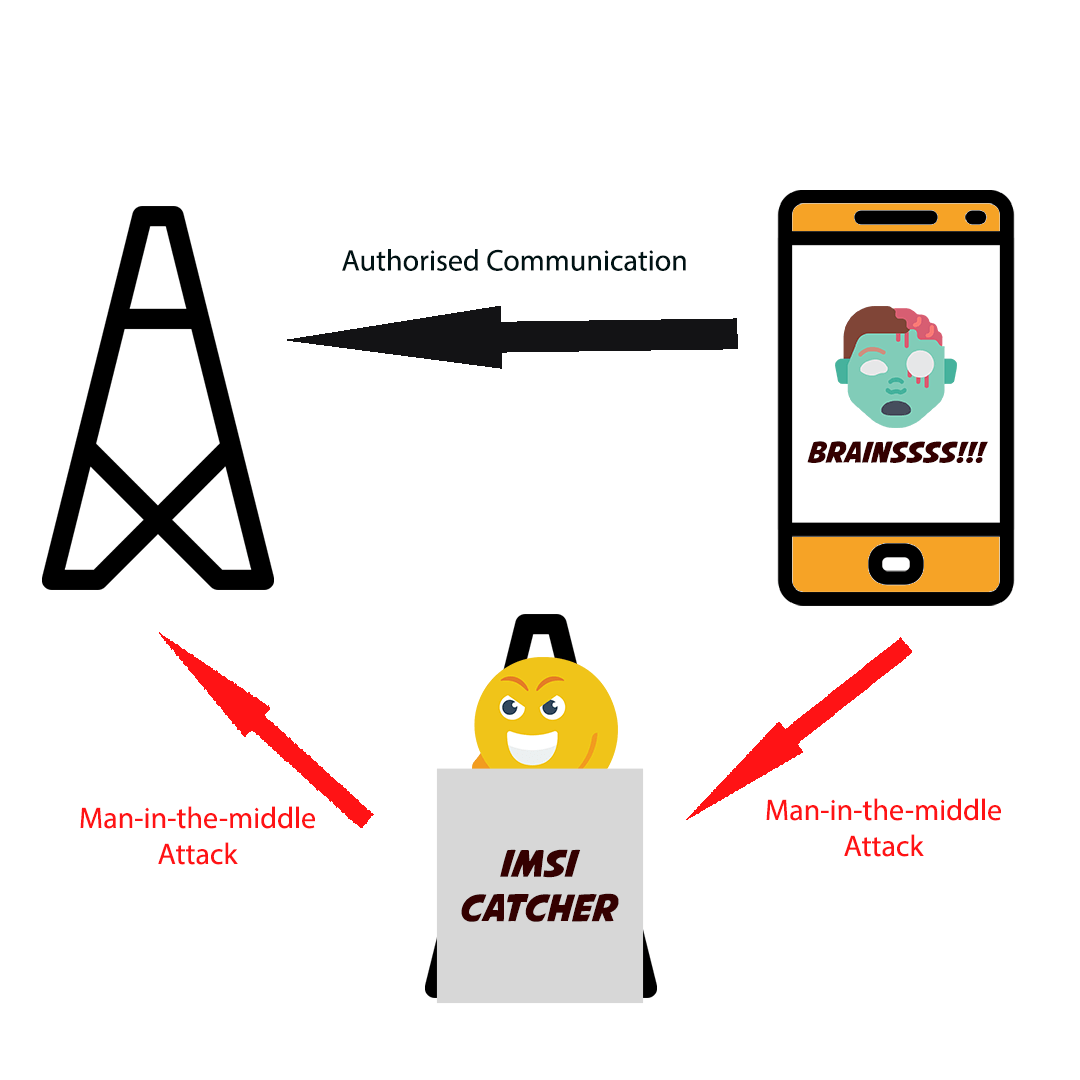
IMSI catchers are sophisticated surveillance hardware often used by law enforcement agencies, but that is not stopping everyday hackers from creating their own homemade versions.
How an IMSI works is by pretending to be a base station or cell tower and deceiving all mobile phones within a certain radius to log into it. Any communication that then comes through can be easily collected, read or even listened on in real time.
And if that isn’t scary enough, all this happens without the victim even knowing. Just like hacking into a mobile phone using public Wi-Fi, hacking into someone’s mobile phone remotely with an IMSI catcher is also a form of a man-in-the-middle attack.
How to hack someone’s phone remotely - the solution?
Mobile communication is becoming more ubiquitous everyday, and as more people connect on mobile devices like cell phones and tablets, techniques for how to hack someone’s phone remotely in 2020 are only bound to increase. As mobile phone users, we need to take start taking urgent steps to protect our personal data privacy. Read our guide on how to find out if your phone has been hacked by someone, and take these 5 steps to keep yourself safe.
This is no one-size-fits-all solution to preventing someone from hacking your phone remotely (unless you’re perfectly fine with using an analog phone), but one good step to take is obtaining a second phone number with Phoner. By masking your actual phone number, remote mobile phone hacking methods that rely on knowing your phone number will instantly become ineffective. With Phoner, you get privacy with reliable calling at no-contract, low-cost options.
Those are just a few ways how to hack someone's phone remotely in 2020. So what are you waiting for? Download Phoner now and start your 2020 by keeping yourself safe from remote cell phone hacks!

 4.5/5 on App Store
4.5/5 on App Store





